This article describes the Intelligence Card Extension for Shodan.
![]()
About Shodan
Shodan is the world's first search engine for internet-connected devices. Shodan continually scans IP Addresses in the Internet-routed IPv4 and IPv6 address space. These scans are performed non-sequentially from multiple global points of presence, and provide a recent and non-attributable snapshot of services hosted at the scanned IP Address.
Shodan scans a broad range of ports at each IP Address, and evaluates the response from each port against behavior signatures for various services. As part of this evaluation, Shodan also assesses whether the host is vulnerable to several specific vulnerabilities. Shodan captures and stores the port scan responses as part of its scan history.
More information about Shodan's scanning methodology is available at the Shodan website.
In addition to this extension, Shodan IoT intelligence is also available in Vulnerability and Infrastructure Lists.
You can enrich any IP address, vulnerability, and domain intelligence card with a live lookup of recent Shodan information.
Analysts using Recorded Future can access Shodan through this extension as part of their Recorded Future subscription. The extension does not need to be configured with Shodan API credentials.
The extension runs automatically when an IP Address card is loaded.
Extending IP Address Cards
Shodan provides rich technical information and enriches IP Address Cards with the following threat intelligence:
- Country
- Organization
- Operating System
- ISP
- Last Update date
- Autonomous System Number (ASN)
- Known vulnerabilities (including vulnerabilities known to be patched and hence 'safe' on this site)
- Device use tags such as "ics", "vpn", or "honeypot"
- Open ports, common uses (as per the Shodan Book's Appendix D, "List of Ports"), and associated scan response banner data from each port -- including history from past scans.
- Note (1): because port history is included, not all ports listed may be currently open.
- Note (2): The "common uses" is for reference only, and does not definitively mean the port is used in the manner listed in the extension. A common point of confusion is when port 80 shows up with common uses as "(HTTP, malware)". This just means that servers with port 80 open often expect HTTP traffic, but certain malware have been also known to use port 80 for comms as well.
Known vulnerabilities are reported using risk tags for the host, which indicate whether host services are vulnerable or not vulnerable to a specific set of CVEs
You can pivot in Recorded Future on these elements of the Shodan response:
- ASNumber
Example (for IP 66.175.83.156):
Another example from an IP tagged as a honeypot (58.213.132.158):
Finally, another example of an IP (217.110.120.250) that appears to be checked for (and is safe from) a vulnerability (CVE-2014-0160); unfortunately, it's at risk for a different vulnerability (CVE-2015-0204):
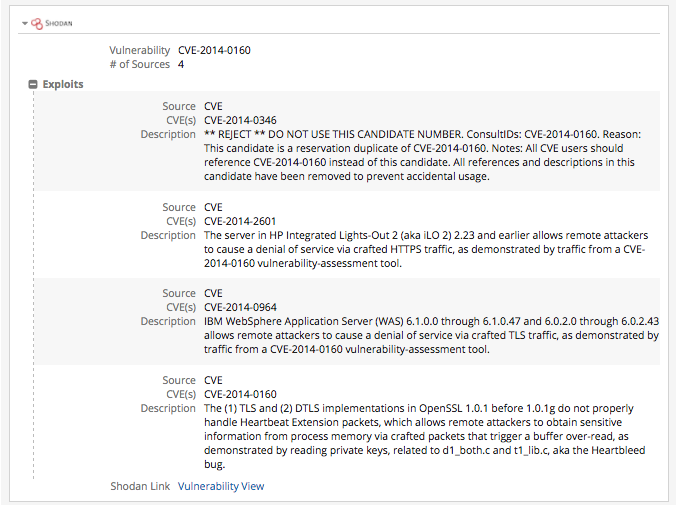
Extending Vulnerability Cards
The Shodan extension will retrieve information from ExploitDB and show the documented exploits as follows:
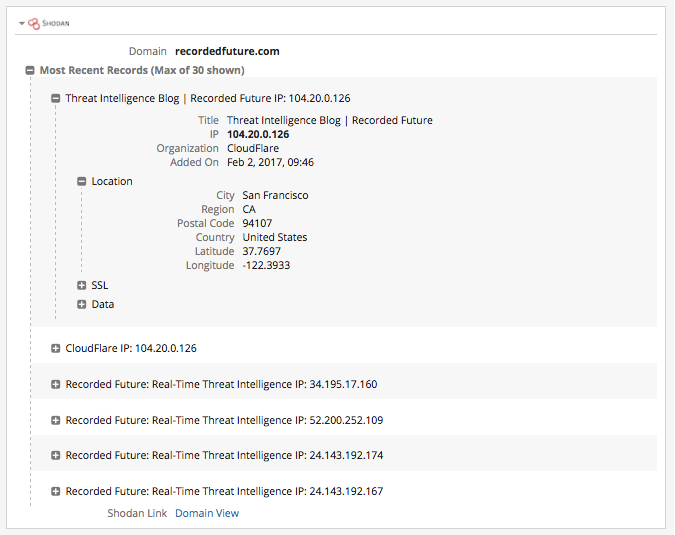
Extending Domain Cards
The Shodan extension will also provide information collected from domains, including IPs, locations, and SSL info:
More Information:
Detailed docs on the various information fields can be found on the Shodan website.