What is Splunk?
Splunk is a platform for investigating large amounts of log data. In recent years it has become one of the leading tools for Cybersecurity teams to manage their network security.
What types of data do clients use in Splunk?
Internal network, system, and application logs generate records of IP addresses, Domains, File Hashes and URLs associated with inbound and outbound network traffic. Clients also routinely put results of Vulnerability scans into Splunk to prioritize patch efforts.
What type of network hardware generates logs monitored in Splunk?
- Endpoint Security Solutions, which include Carbon Black, Symantec, Tanium, McAfee, Kaspersky, Trend Micro, Microsoft, Crowdstrike, FireEye HX, Cylance, and ClamAV, assist in identifying and blocking risks such as malware or user abuse, to endpoint systems. Clients can typically collect hashes from these services.
- Firewalls, which include Cisco PIX, Cisco ASA, Juniper (SSPs), Sonicwall, and IPTables, control network traffic at the network perimeter by allowing or denying packets based on rules regarding source and destination addresses. Clients can typically collect IP addresses from these appliances and services.
- Next Gen Firewalls, offered by Palo Alto Networks, Cisco Firepower, Juniper NRX, Checkpoint, and Fortinet, offer security services similar to traditional firewalls, but include more dynamic features such as adaptive rules and netflows. Clients can typically collect IPs, Domains, and Hashes from these appliances.
- Application firewalls, such as F5, Imperva, Akamai, and Cloudflare behave similarly to network firewalls, but provide access controls to application endpoints. Clients can typically collect IP addresses from these services.
- Proxies, offered by Symantec (Bluecoat), ZScaler, McAfee, Cisco WSA, HAproxy, Squid, and Proofpoint Proxy DLP, manage web traffic via an intermediary server. This allows organizations to funnel Internet-bound traffic through a single server or a limited number of servers for improved content monitoring and management. Clients can typically collect IPs, Domains, and Hashes from these appliances.
- Internal DNS Resolvers include Bind, Infoblox, and Microsoft DNS Services. Clients use these servers to provide authoritative name resolution for internal and external domains they control. Logs from these services can help identify DNS abuse such as DNS tunneling and zone transfers. Clients can typically collect Domains from these services.
- Intrusion Detection Systems / Intrusion Prevention Systems (IDS/IPS), offered by FireEye NX, SourceFire (Cisco), Tenable, McAfee, SNORT, Bro, Security Onion and IBM, detect or prevent unauthorized network access using a variety of techniques. Clients can typically collect IP addresses, Domains, Hashes, and Vulnerabilities from these appliances.
- Web Server Logs from servers such as Apache, Tomcat, Microsoft IIS, JBoss, and Nginx provide information that can be used to identify suspicious or malicious activity on Web servers. Clients can typically collect IP addresses from these logs.
- Vulnerability Scanners such as Qualys, Tenable, and Rapid7 identify vulnerabilities on network hosts and quantize vulnerability risk. Clients can typically collect Vulnerability reports from these services that tabulate information about vulnerabilities found in the client environment including the number and type of device (end user machine vs server) affected.
- Email Gateways, such as Proofpoint, Forcepoint, McAfee, SMTP, and Ironport (ESA), allow organizations to monitor for email abuse such as phishing, spam, or malicious attachments and prevent data loss by analyzing outgoing emails and attachments. Clients can typically collect Domains and Hashes from these services.
What is a DMZ?
- An area in the security architecture where inbound external traffic is allowed to a public accessible network through the firewall. Both inbound and outbound traffic is mediated by the firewall.
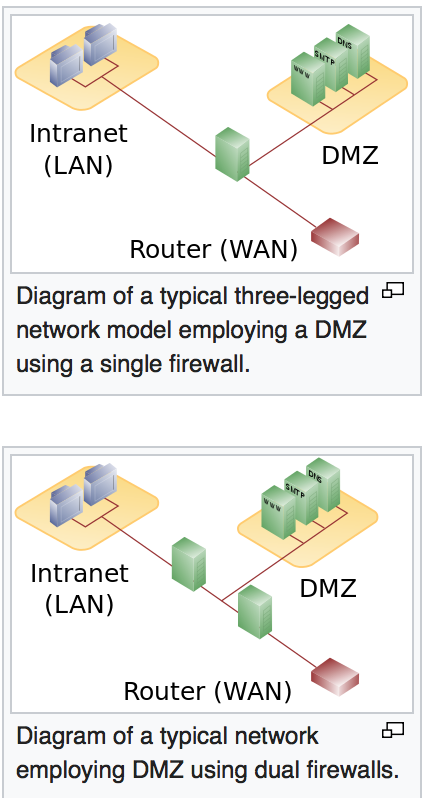
Which Data types are typically inbound or outbound?
- IP addresses are most often observed in inbound logs as IP addresses sending traffic into the network and internal machines responding
- Inbound IP data is typically observed in the Firewall to DMZ’s, Externally Facing Application Servers, and Application FIrewalls
- Outbound IP data is typically observed in Proxies and Firewalls
- Domains and URLs are typically observed typically network traffic originating internal to the system and headed out
- Some companies resolve domains to IP addresses internally with their own DNS servers. These logs will have the domains internal machines are attempting to communicate with and the associated IP addresses
- Hashes are observed inbound as internal machines are downloading files from the web and outbound when internal systems are communicating to external endpoints. Presence of malicious files on outbound traffic is indicative of infected internal machines.
What Use Cases do we support?
At a high level we support 5 main use cases.
- Enrichment: Allow Splunk user to dynamically retrieve and display Intelligence card content when researching individual Indicators. Provides deep context for Indicators being investigated due to triggering alerts for any reason
- Correlation: Generate “Notable Events” based on an indicator in a client log matching one of Recorded Future Risk Lists
- Correlation searches should take into account the log sources, and not just blindly correlate against all available client log data. For example, only "accepted" firewall traffic should be correlated to Recorded Future risklists; on the other hand, only IPS/IDS traffic resulting in an alert is recommended for Recorded Future correlation. Professional services can assist in more detailed discussions.
- Vulnerability Assessment (Splunk Enterprise only): Combine client vulnerability scans with our Risk Scores and associated awareness of Pre NVD release publication, exploits in the wild, etc., to perform an assessment of highest impact vulnerabilities
- Alert Review: Configure Recorded Future alerts to be received in Splunk
- SOC Display: Display summary information about Recorded Future risk lists and alerts via visual and tabular objects (Splunk Enterprise only)
Much more detail on these is available in the Intelligence Goal Document [link to be provided shortly]
What are the major versions of Splunk we need to understand?
- Splunk Enterprise or "Core Splunk" is the base platform. It is extremely configurable and can support a wide variety of use cases. Companies typically have or outsource Splunk experts to configure dashboards/workflows that support their internal work processes
- Our Splunk Enterprise app is often a proof of concept for organizations with Splunk Enterprise. Clients are likely to look at our correlation and enrichment page and integrate the functionality they want into their own dashboards
- All Use cases supported
- Splunk Enterprise Security (Splunk ES) is a set of functionality added to Splunk Enterprise explicitly for security use cases. Splunk ES comes pre-configured with dashboards to monitor overall security posture, incident response, threat monitoring, and other use cases. It also uses several custom data models to normalize security-related data for easier consumption and analysis. Many organizations use Splunk ES as their Security Information and Event Management (SIEM) platform.
- Splunk ES supports minimal configurability. Our integration with Splunk ES requires little configuration and limited functionality.
- We recommend Splunk ES Users use both of our apps; our Splunk ES app to take advantage of its default functionality and our Splunk Enterprise app for the broader use cases it supports.
- Correlation and Enrichment Use cases are supported.
- Splunk Cloud provides the same service as Splunk Enterprise, including support for Splunk ES and Splunk apps, but moves the storage and processing of data into a cloud-based service. This removes the need for installation of on-premises appliances for the client's Splunk installation. Splunk staff also manage the instance in Splunk Cloud and hence installation of apps (and other application maintenance) requires the client to file a ticket with Splunk. Furthermore, Splunk will only install apps to a Splunk Cloud instance that have been certified, while non-certified apps may be installed on on-premises instances of Splunk at the client's discretion. Furthermore, any customization of the scripts in Splunk Cloud will require a review cycle that may take up to four weeks.
What Recorded Future features are relevant for a Splunk integration?
- Dynamic Enrichment is supported via the Connect API features for retrieving indicator context.
- Risklists from Recorded Future are downloaded using the Connect API to support correlation
- Base Risklists are downloaded as scheduled and used for default correlation dashboards. These can be integrated with custom dashboards as well
- Longer Risklists are available for additional use cases requiring custom configuration
- FUSION can be used to create Customized Risklists based on integrating Recorded Future, Client, and Third Party feeds as necessary and to deliver these custom feeds to Splunk
- Splunk Apps
- We ship two splunk apps, Recorded Future Add-on for Splunk ES and Recorded Future App for Splunk.
- These apps access the Connect and Fusion APIs
How does the Splunk integration vary by Module?
The Splunk Integration can be purchased with any Recorded Future module, or combination of modules; however, different parts of the integration will or will not work based on the integrations purchased. To further explain, there are different use cases that each module supports, and when the Splunk integration is purchased in combination with a module, those module-specific use cases will be enabled. One way to think of it is this: We packaged all of the functionality available for Splunk, across all modules, into a single application. Turning on different functions will depend on the subscriptions the client has signed up (and paid) for.
Here is a table showing which Splunk integration features should work with which modules:
| Feature | SecOps | Brand | Threat Intel | Vuln | Third-Party | Geopol |
| Config | Yes | Yes | Yes | Yes | Yes | Yes |
| Enrich: IP | Yes | Yes | Yes | n/a | n/a | n/a |
| Enrich: Domain | Yes | Yes | Yes | n/a | n/a | n/a |
| Enrich: Hash | Yes | n/a | Yes | n/a | n/a | n/a |
| Enrich: Vuln | n/a | n/a | n/a | Yes | n/a | n/a |
| Enrich: Malware | Yes | n/a | Yes | n/a | n/a | n/a |
| Enrich: URL | Yes | Yes | Yes | n/a | n/a | n/a |
| Correlate: IP | Yes | n/a | Yes | n/a | n/a | n/a |
| Correlate: Domain | Yes | n/a | Yes | n/a | n/a | n/a |
| Correlate: Hash | Yes | n/a | Yes | n/a | n/a | n/a |
| Correlate: Vuln | n/a | n/a | n/a | Yes | n/a | n/a |
| Correlate: URL | Yes | n/a | Yes |
n/a |
n/a | n/a |
| SOC: Alerts | n/a | Yes | Yes | Yes | n/a | n/a |
| SOC: Global Map | Yes | Yes | Yes | Yes | n/a | n/a |
| Other: (all) | Yes | Yes | Yes | Yes | Yes | Yes |
Where can I learn more about Splunk?
https://www.splunk.com/en_us/view/education/SP-CAAAAH9