This is the most common integration use case. Typically, a partner application workflow may lead to a single or small set of entities that require additional context (e.g., an IP address from which suspicious traffic has been observed, or an unpatched server with a known vulnerability of unknown risk). Enrichment integrations tap into Recorded Future's extensive and rich context to pull in risk scores, risk evidence, related entities, and examples references from various source types (e.g., social media, security research blogs, dark web).
As a general principle, anything information available on an intelligence card is available via the Connect API. Integrations seeking to replicate the content in an Intelligence card within the partner application can make a API single request to get all the data in json format. It is then up to the partner application (and associated integration code) to display the threat intelligence data appropriately. We recommend using a layout similar to Recorded Future's Intelligence card for consistency of user experience. This approach is useful in situations where the user is not expected to have a license to Recorded Future, and will remain solely within the partner application for his or her workflow.
Some enrichment integrations only utilize a concise and high value portion of the data (usually risk scores, risk evidence, most recent sighting datetime) and include a link back to the intelligence card for further details. This more limited pull of Recorded Future enrichment information is often part of an automated process, and is particularly useful when the user also has a license to Recorded Future and can easily pivot between the partner application and Recorded Future.
Note that enrichment integrations can be setup as both on demand lookups, or in an automated process.
The API Explorer can be used to test and get sample code for different API queries; here's a screen shot showing an enrichment request for an IP address; the explorer allows the developer to choose which fields to display, and the "Try it out!" button will generate sample code and the actual data response.
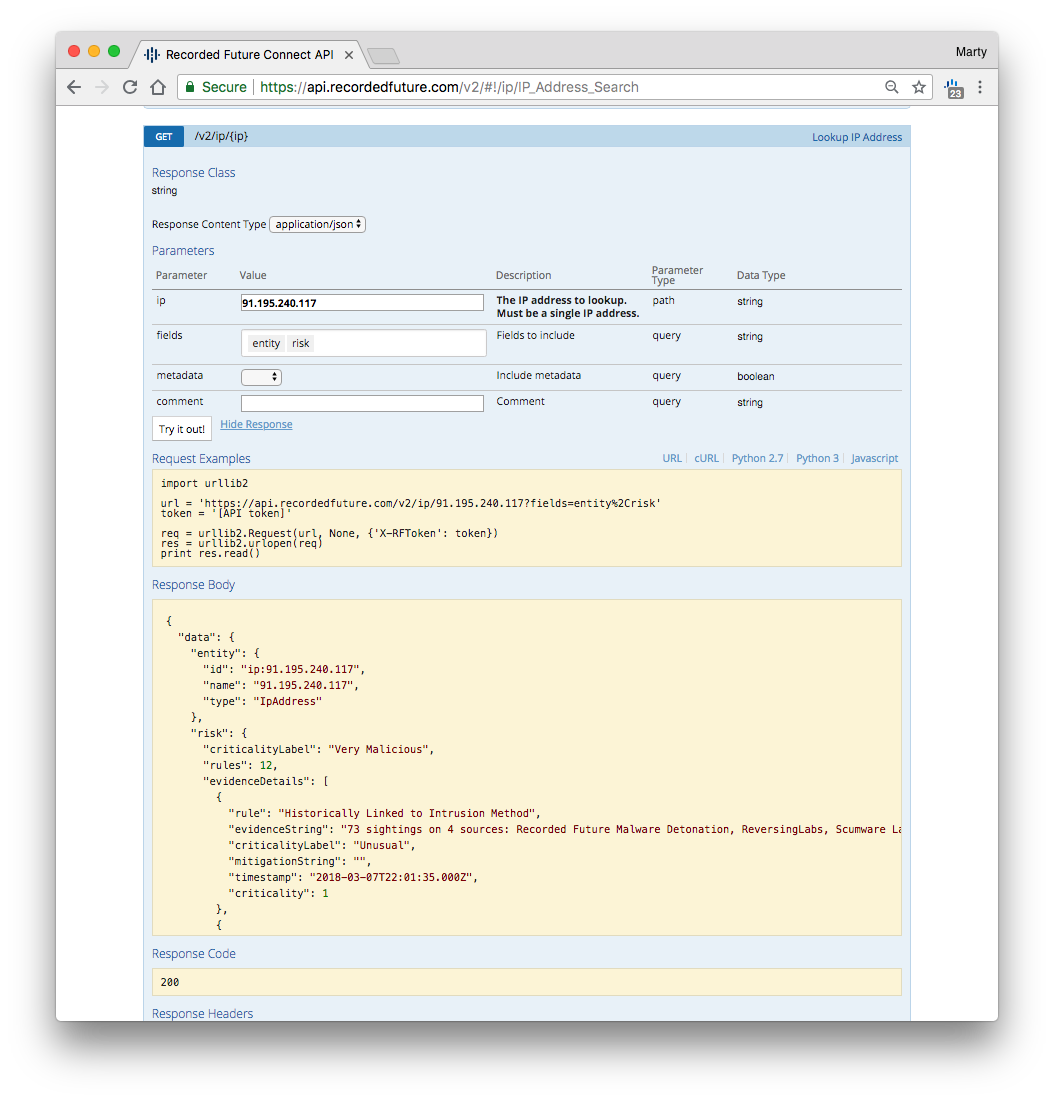
See this support page for additional details in the different filters and fields available via the Connect API.
Example Enrichment Queries:
[1] Getting risk and timestamp information for a specific IP address
cURL command:
curl -H "X-RFToken: [API token]" "https://api.recordedfuture.com/v2/ip/141.212.122.64?fields=entity%2Crisk%2Ctimestamps"
Response:
{
"data": {
"entity": {
"id": "ip:141.212.122.64",
"name": "141.212.122.64",
"type": "IpAddress"
},
"timestamps": {
"firstSeen": "2015-09-08T11:13:02.268Z",
"lastSeen": "2018-08-19T08:26:06.033Z"
},
"risk": {
"criticalityLabel": "Malicious",
"rules": 10,
"evidenceDetails": [
{
"rule": "Historical Honeypot Sighting",
"evidenceString": "674 sightings on 14 sources including: @atma_es, @EvilAfoot, @gosint2, @DansHoneypot, @Combot_Aeneas. Most recent tweet: honeyminer: #HTTP Possible HTTP attack from 141.212.122.64 https://t.co/FLOlfCYGr2. Most recent link (Aug 8, 2018): https://twitter.com/HoneyPyLog/statuses/1027343633941516288",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-08-08T23:59:44.000Z",
"criticality": 1
},
{
"rule": "Historically Linked to Intrusion Method",
"evidenceString": "4 sightings on 2 sources: @olaf_j, @EIS_BFB. 1 related intrusion method: Brute Force Blocking (BFB). Most recent tweet: Masterdeb1 BFB-attack detected from 141.212.122.64 to on 13.06.2018 13:25:02. Most recent link (Jun 13, 2018): https://twitter.com/olaf_j/statuses/1006860044451962881",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-06-13T11:25:15.000Z",
"criticality": 1
},
{
"rule": "Historically Linked to Cyber Attack",
"evidenceString": "381 sightings on 9 sources including: @atma_es, @EvilAfoot, @DansHoneypot, @Combot_Aeneas, @HoneyPyLog. Most recent tweet: #POP3 incoming POP3 attack from 141.212.122.64 https://t.co/PzP5GMttsc. Most recent link (Apr 7, 2018): https://twitter.com/idahohoneypot/statuses/982691878536601605",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-04-07T18:49:36.000Z",
"criticality": 1
},
{
"rule": "Historically Reported by DHS AIS",
"evidenceString": "9 sightings on 1 source: DHS Automated Indicator Sharing. 9 reports including STIX Package, from Anomali, Inc., Information Technology Sector, NCCIC:STIX_Package-92810b61-7446-47fb-bba9-56dc605fcd12 (Feb 2, 2018).",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-02-02T06:50:46.000Z",
"criticality": 1
},
{
"rule": "Historical SSH/Dictionary Attacker",
"evidenceString": "17 sightings on 2 sources: Darrens Website, AbuseIP Database. Most recent link (Jan 8, 2018): https://www.abuseipdb.com/check/141.212.121.162",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-01-08T14:49:18.057Z",
"criticality": 1
},
{
"rule": "Unusual IP",
"evidenceString": "1 sighting on 1 source: Project Turris Attempted Access Greylist.",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-08-22T08:34:53.278Z",
"criticality": 1
},
{
"rule": "Historically Reported in Threat List",
"evidenceString": "Previous sightings on 2 sources: CINS: CI Army List, Taichung City Education Bureau Unusual IP Address Report. Observed between Jun 24, 2018, and Aug 22, 2018.",
"criticalityLabel": "Unusual",
"mitigationString": "",
"timestamp": "2018-08-22T08:34:53.285Z",
"criticality": 1
},
{
"rule": "Recent Honeypot Sighting",
"evidenceString": "2 sightings on 1 source: @HoneyPyLog. Most recent tweet: honeyminer: #DarkIRC Possible DarkIRC attack from 141.212.122.64 https://t.co/FLOlfCYGr2. Most recent link (Aug 19, 2018): https://twitter.com/HoneyPyLog/statuses/1031094900811554816",
"criticalityLabel": "Suspicious",
"mitigationString": "",
"timestamp": "2018-08-19T08:25:55.000Z",
"criticality": 2
},
{
"rule": "Recent Multicategory Blacklist",
"evidenceString": "1 sighting on 1 source: Alienvault: IP Reputation Data.",
"criticalityLabel": "Suspicious",
"mitigationString": "",
"timestamp": "2018-08-22T08:34:53.277Z",
"criticality": 2
},
{
"rule": "Recently Linked to Intrusion Method",
"evidenceString": "2 sightings on 1 source: @HoneyPyLog. 1 related intrusion method: Darkirc. Most recent tweet: honeyminer: #DarkIRC Possible DarkIRC attack from 141.212.122.64 https://t.co/FLOlfCYGr2. Most recent link (Aug 19, 2018): https://twitter.com/HoneyPyLog/statuses/1031094900811554816",
"criticalityLabel": "Malicious",
"mitigationString": "",
"timestamp": "2018-08-19T08:25:55.000Z",
"criticality": 3
}
],
"riskSummary": "10 of 49 Risk Rules currently observed.",
"criticality": 3,
"riskString": "10/49",
"score": 85
}
}
}