This page is intended to help you use the Intelligence Card Extensions for Hash Intelligence Cards:
|
Applicable Intelligence Card: |
Hash Card |
|
Applicable Intelligence Partners: |
Palo Alto Autofocus, PhishMe, ReversingLabs |
Step 1: Identify a suspicious file hash
- The top hash indicators from the Cyber Dashboard are often good starting points for an investigation. Note that it is not uncommon to find hashes without hits in one or more of the extensions, so don't be surprised if you need to try a few hashes before finding one with any extension data.
- Note that the PhishMe Extension can be slow in returning a response; they are aware of the issue and working on improving performance.
- For illustrative purposes, here is a list of selected hashes with known extension responses:
|
Hash |
Has Data? |
||
|
Palo Alto Autofocus |
PhishMe |
ReversingLabs |
|
|
03718676311de33dd0b8f4f18cffd488 |
Yes |
No |
Yes |
|
12c9c0bc18fdf98189457a9d112eebfc |
Yes |
No |
Yes |
|
80132a037cbef3cd8e801f330c0522d0 |
Yes |
Yes |
Yes |
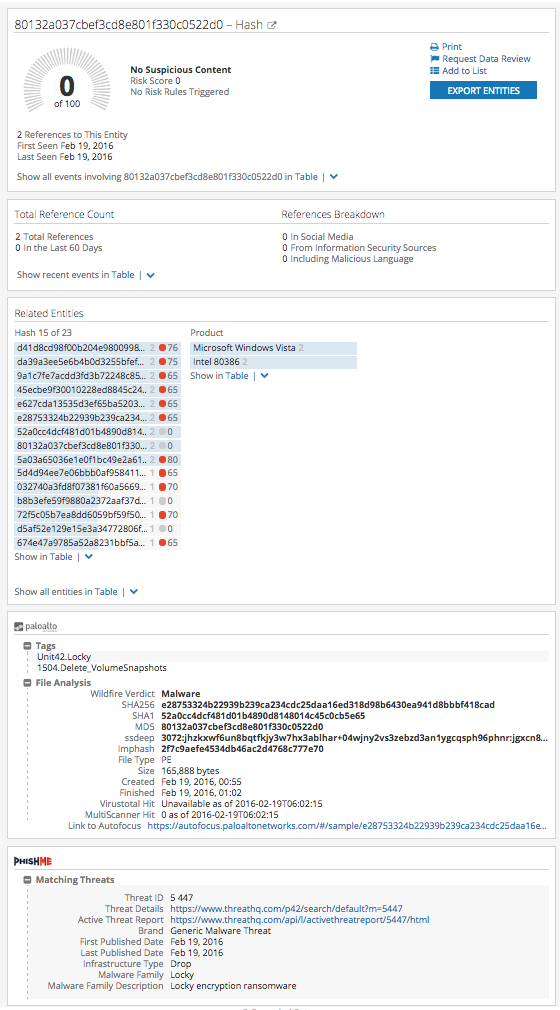
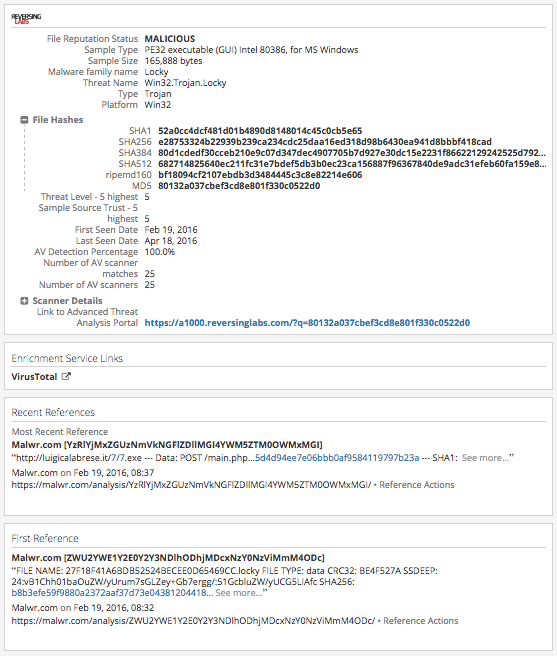
- This last hash (80132…) is a good example because at present (June 6, 2016) the hash has a risk score of 0 and has many high-risk IPs as 'related entities'. The hits from Palo Alto, PhishMe, and ReversingLabs reveal that it is indeed a malicious hash. Screen shot included below:
Step 2: Open the Recorded Future Hash Intelligence Card for this hash
- You can click on the hash in the Cyber dashboard, or type the hash into the Quick Search box
Step 3: Click "Lookup" for the extensions you have enabled for your account
- Below is an example of a Hash Intelligence Card including the lookup (expanded) of Palo Alto Networks' Autofocus, PhishMe, and ReversingLabs data: